SIEM
Intelligent threat detection and investigation for dynamic environments.
Apica’s SIEM solution delivers enterprise-grade security intelligence through real-time log analysis, advanced threat detection, and automated incident response. By leveraging open-source technology and seamless infrastructure integration, we centralize security monitoring across your entire organization.
From comprehensive log management to sophisticated event correlation, Apica SIEM provides the tools needed to identify, analyze, and neutralize security threats before they impact your operations, while ensuring regulatory compliance and maintaining robust security posture.
problem
Security challenges
Security Data Fragmentation
Scattered security data across sources and systems hinders comprehensive threat visibility and analysis.
Delayed Threat
Response
Centralized monitoring prevents time wasted on manual data collection and correlation, enabling faster threat response
Limited Network Visibility
Traditional security creates blind spots, fragmenting infrastructure visibility and leaving organizations vulnerable to attacks.
Manual Security Operations
Manual threat correlation limits security teams' incident detection and response capabilities.
Compliance Management Complexity
Inconsistent security compliance results from fragmented logging and poor audit trails.
BENEFITS
Apica’s unified security intelligence for threat detection and response

Unified Security Intelligence

Real-Time Threat Detection

Automated Incident Response

Advanced Log Analytics

Seamless
Integration

Comprehensive Compliance Management
FEATURES
Every control. At your fingertips.
Detect threats in real-time
Continuously monitor and analyze to identify potential risks and vulnerabilities, fortifying security posture.
Stay ahead of emerging threats by leveraging advanced analytics and machine learning techniques.
Streamline incident response
Accelerate investigation and remediation processes, minimizing security incident impact on the organization.
Implement automation to expedite response times and reduce manual intervention.
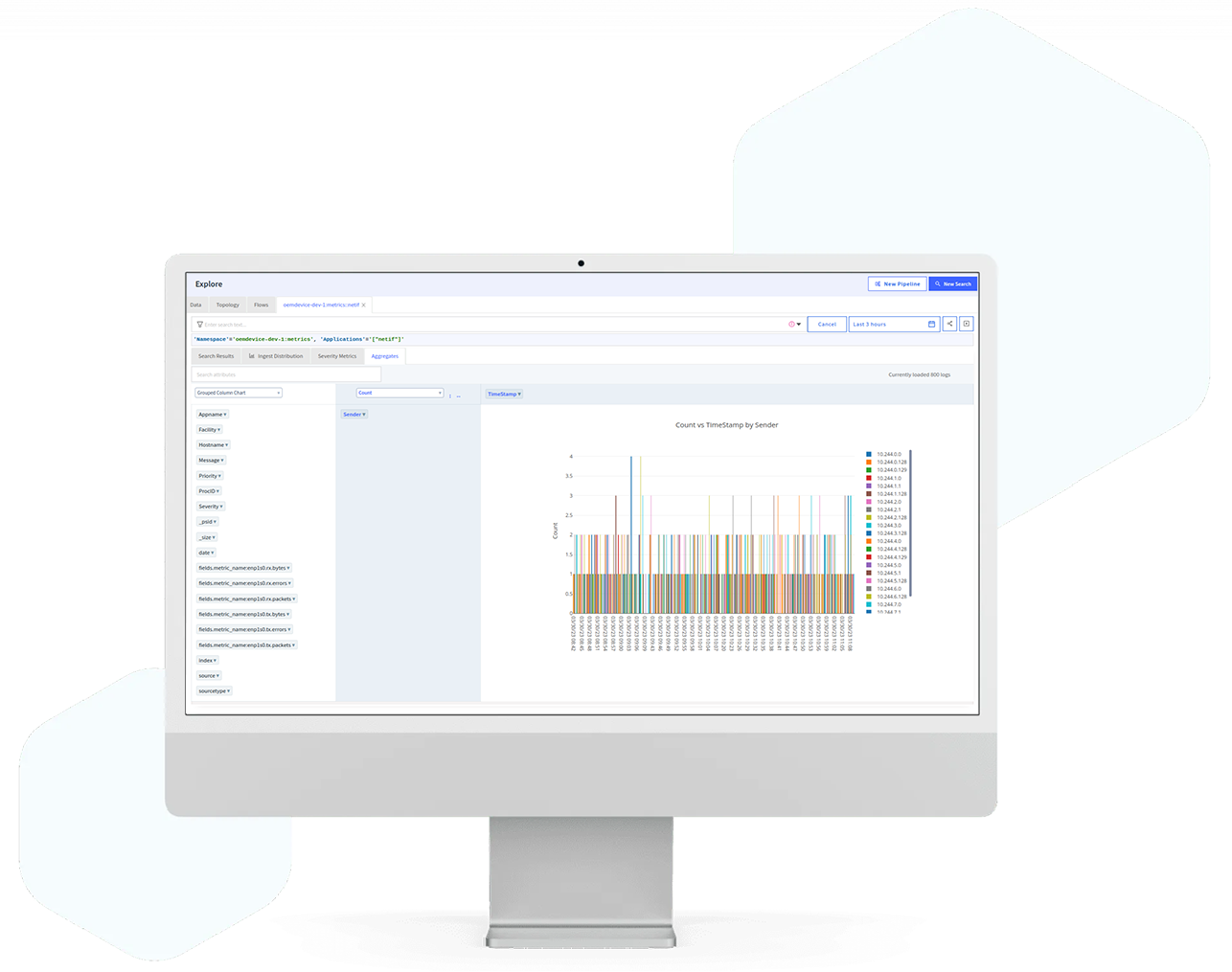
Analyze logs comprehensively
Aggregate and process log data from various sources, delivering actionable insights for informed decisions.
Utilize advanced search capabilities and visualization tools to make sense of complex data.
Enhance security intelligence
Access detailed, customizable reports and dashboards for better understanding of the security landscape.
Stay informed with real-time updates, trends, and alerts to maintain a proactive security stance.
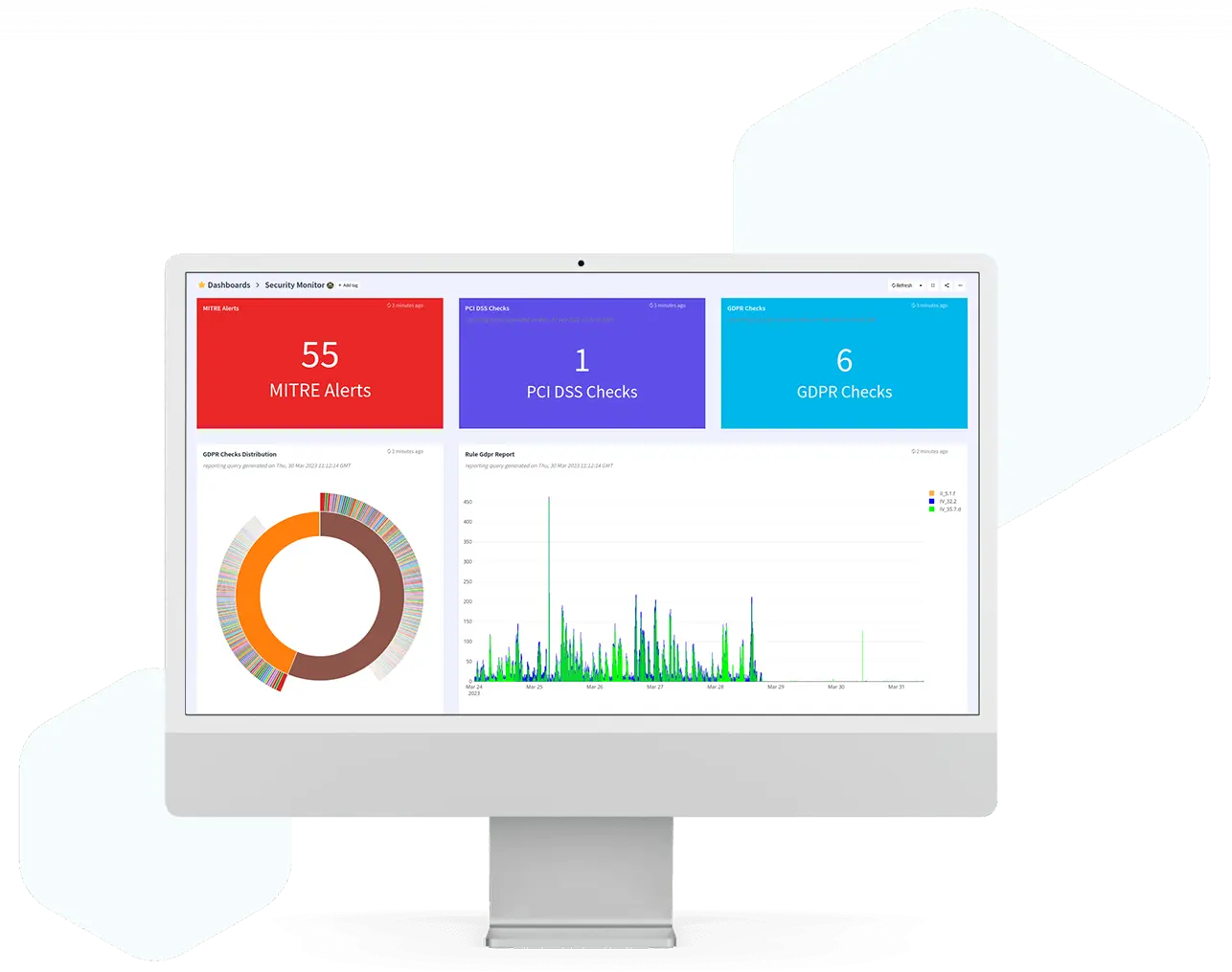
More Features
Simplify compliance monitoring
Adhere to various compliance standards with ease, reducing risks of penalties and reputational damage.
Assess vulnerabilities effectively
Identify and prioritize system vulnerabilities, targeting resources efficiently to minimize potential threats.
Monitor file integrity
Keep an eye on critical system files for unauthorized modifications, ensuring data integrity and preventing breaches.
Analyze anomalies and behavior
Spot unusual patterns and user activities, enabling rapid response to potential security incidents.
Integrate with existing infrastructure
Connect seamlessly with current systems, enhancing capabilities and providing a unified security solution.
Embrace scalability and flexibility
Adapt to organizational needs, accommodating growth and evolving security requirements for lasting protection.
INTEGRATE WITH ANY STACK



*Trademarks belong to the respective owners.







