SIEM
Empower Threat Detection.
Streamline Incident Response.
Revolutionize Security Intelligence.
problem
Are you struggling to handle
vast data from complex, distributed systems efficiently?

Inadequate threat detection?

Slow incident response times?

Insufficient security intel?

Disjointed security and alerts?

Difficulty adhering to compliance?

Overwhelmed security teams?
BENEFITS
We Can Help.
See How.
detection
response
insights
integration
compliance
management
resources
FEATURES
Every control.
At your fingertips.
Detect threats in real-time
Continuously monitor and analyze to identify potential risks and vulnerabilities, fortifying security posture.
Stay ahead of emerging threats by leveraging advanced analytics and machine learning techniques.
Streamline incident response
Accelerate investigation and remediation processes, minimizing security incident impact on the organization.
Implement automation to expedite response times and reduce manual intervention.
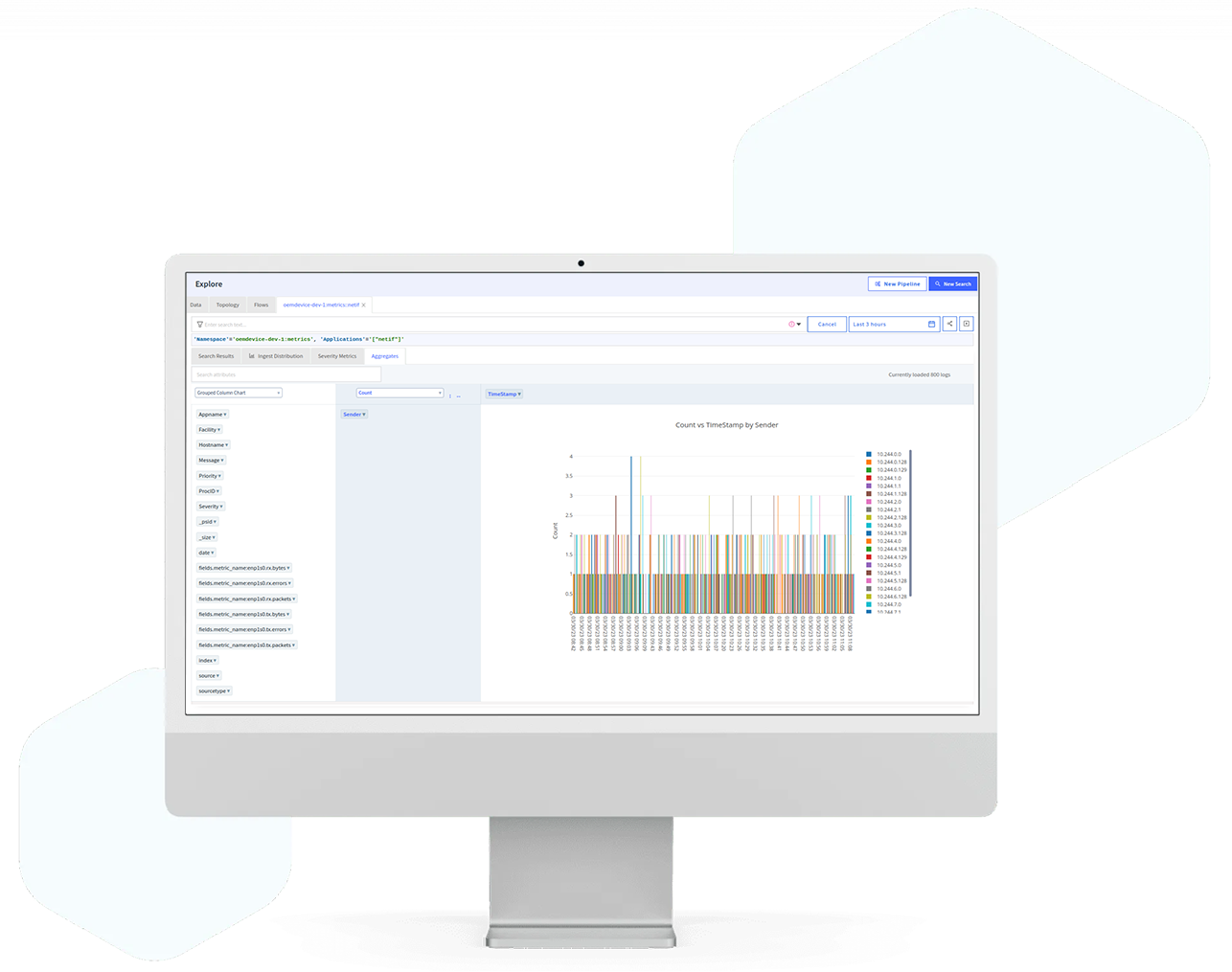
Analyze logs comprehensively
Aggregate and process log data from various sources, delivering actionable insights for informed decisions.
Utilize advanced search capabilities and visualization tools to make sense of complex data.
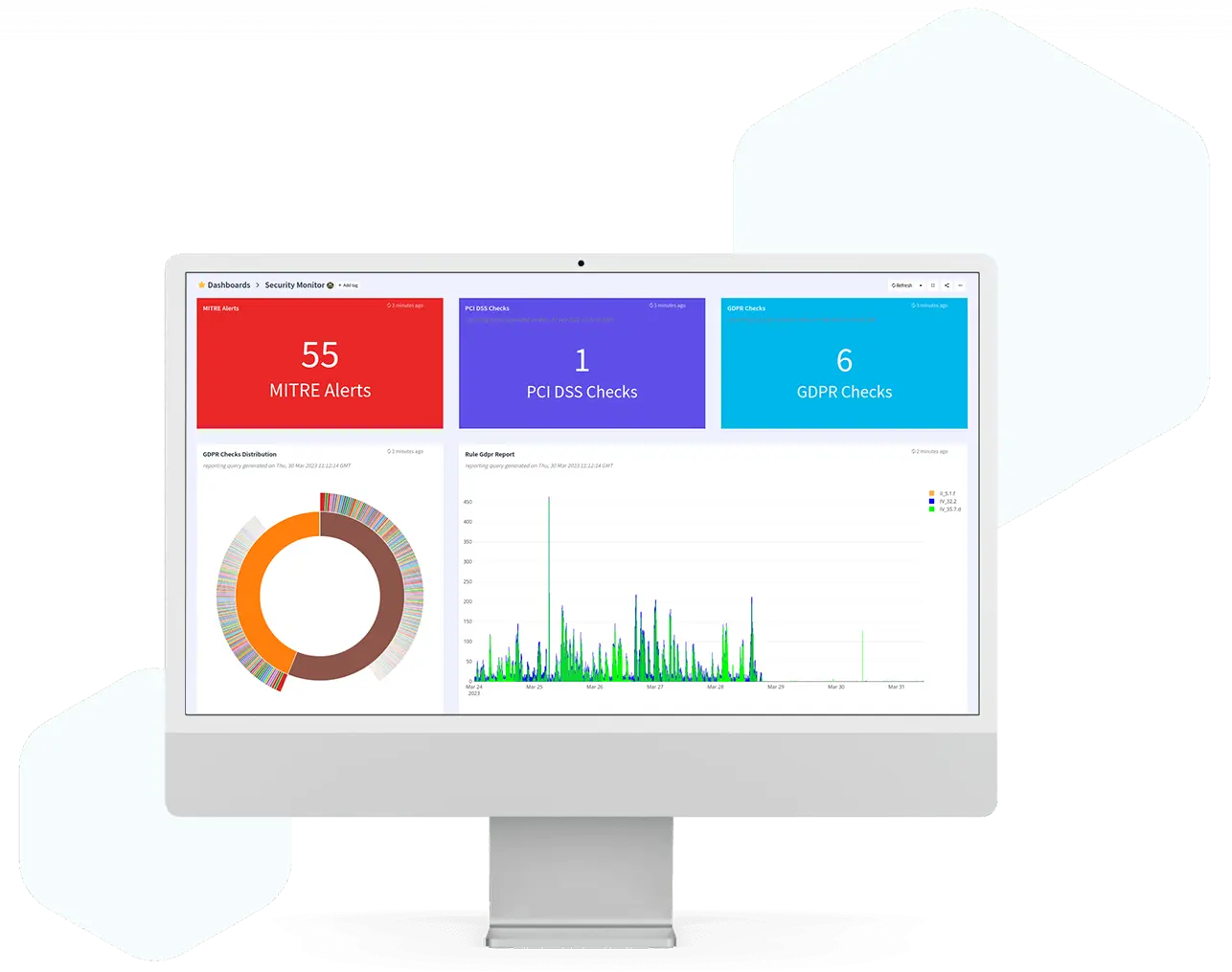
Enhance security intelligence
Access detailed, customizable reports and dashboards for better understanding of the security landscape.
Stay informed with real-time updates, trends, and alerts to maintain a proactive security stance.
Get our Comprehensive Logs Data Sheet right into your Inbox
More Features
Simplify compliance monitoring
Adhere to various compliance standards with ease, reducing risks of penalties and reputational damage.
Assess vulnerabilities effectively
Identify and prioritize system vulnerabilities, targeting resources efficiently to minimize potential threats.
Monitor file integrity
Keep an eye on critical system files for unauthorized modifications, ensuring data integrity and preventing breaches.
Analyze anomalies and behavior
Spot unusual patterns and user activities, enabling rapid response to potential security incidents.
Integrate with existing infrastructure
Connect seamlessly with current systems, enhancing capabilities and providing a unified security solution.
Embrace scalability and flexibility
Adapt to organizational needs, accommodating growth and evolving security requirements for lasting protection.
INTEGRATE WITH ANY STACK



*Trademarks belong to the respective owners.
PRICING
Reclaim control of data, cost and complexity.
SECURE
Edge
Protection
Secure your enterprise with powerful extended security.
| Free Plan^ | Upto 20 Hosts |
| Self-hosted | $5/Host/mo |
| SaaS | $5/Host/mo* |
- Host intrusion detection (HIDS).
- SIEM and SOAR.
- Multi-petabyte scale.







